Code-execution flaw in VMware has a severity rating of 9.8 out of 10

Hackers are mass-scanning the Internet in search of VMware servers with a newly disclosed code-execution vulnerability that has a severity rating of 9.8 out of a possible 10.
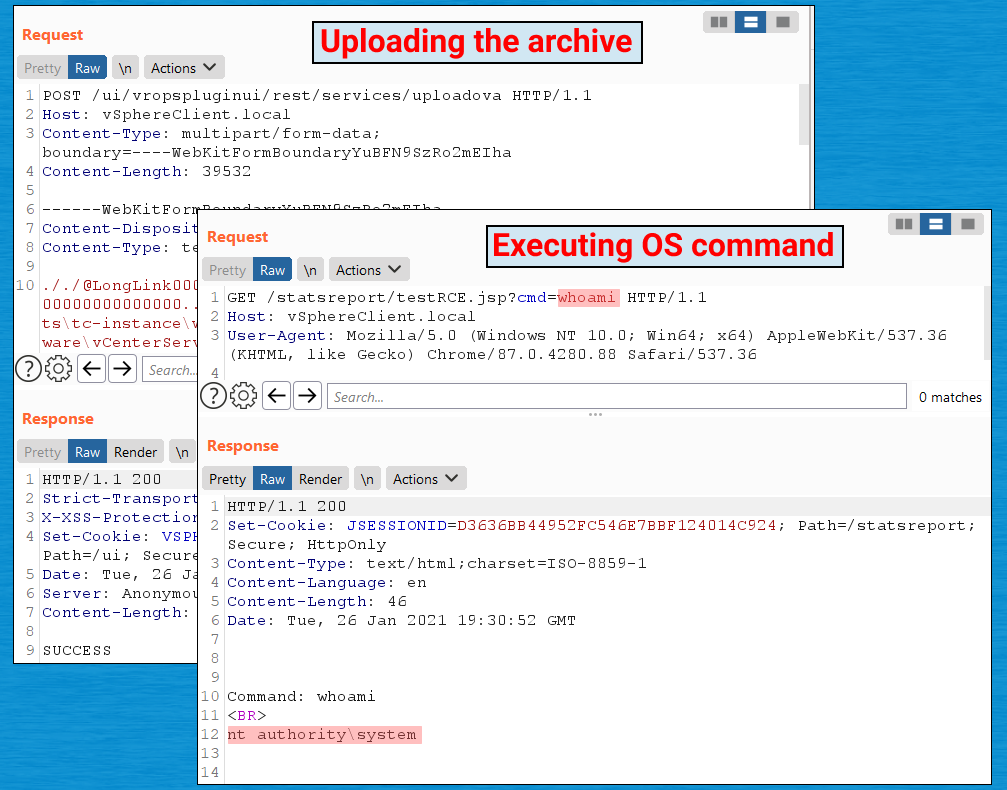
CVE-2021-21974, as the security flaw is tracked, is a remote code-execution vulnerability in VMware vCenter server, an application for Windows or Linux that administrators use to enable and manage virtualization of large networks. Within a day of VMware issuing a patch, proof-of-concept exploits appeared from at least six different sources. The severity of the vulnerability, combined with the availability of working exploits for both Windows and Linux machines, sent hackers scrambling to actively find vulnerable servers.
“We’ve detected mass scanning activity targeting vulnerable VMware vCenter servers (https://vmware.com/security/advisories/VMSA-2021-0002.html),” researcher Troy Mursch of Bad Packets wrote.
Mursch said that the BinaryEdge search engine found almost 15,000 vCenter servers exposed to the Internet, while Shodan searches revealed about 6,700. The mass scanning is aiming to identify servers that have not yet installed the patch, which VMware released on Tuesday.
Unfettered code execution, no authorization required
CVE-2021-21972 allows hacker with no authorization to upload files to vulnerable vCenter servers that are publicly accessible over port 443, researchers from security firm Tenable said. Successful exploits will result in hackers gaining unfettered remote code-execution privileges in the underlying operating system. The vulnerability stems from a lack of authentication in the vRealize Operations plugin, which is installed by default.
The flaw has received a severity score of 9.8 out of 10.0 on the Common Vulnerability Scoring System Version 3.0. Mikhail Klyuchnikov, the Positive Technologies researcher who discovered the vulnerability and privately reported it to VMware, compared the risk posed by CVE-2021-21972 to that of CVE-2019-19781, a critical vulnerability in the Citrix Application Delivery Controller.
The Citrix flaw came under active attack last year in ransomware attacks on hospitals, and according to a criminal indictment filed by the Justice Department, in intrusions into game and software makers by hackers backed by the Chinese government.
In a blog post earlier this week, Klyuchnikov wrote:
In our opinion, the RCE vulnerability in the vCenter Server can pose no less a threat than the infamous vulnerability in Citrix (CVE-2019-19781). The error allows an unauthorized user to send a specially crafted request, which will later give them the opportunity to execute arbitrary commands on the server. After receiving such an opportunity, the attacker can develop this attack, successfully move through the corporate network, and gain access to the data stored in the attacked system (such as information about virtual machines and system users). If the vulnerable software can be accessed from the Internet, this will allow an external attacker to penetrate the company’s external perimeter and also gain access to sensitive data. Once again, I would like to note that this vulnerability is dangerous, as it can be used by any unauthorized user.
The researcher provided technical details here.
CVE-2021-21972 affects vCenter Server versions 6.5, 6.7, and 7.01. Users running one of these versions should update to 6.5 U3n, 6.7 U3l, or 7.0 U1c as soon as possible. Those who can’t immediately install a patch should implement these workarounds, which involve changing a compatibility matrix file and setting the vRealize plugin to incompatible. Admins who have vCenter servers directly exposed to the Internet should strongly consider curbing the practice or at least using a VPN.