Cryptocurrency launchpad hit by $3 million supply chain attack

SushiSwap’s chief technology officer says the company’s MISO platform has been hit by a software supply chain attack. SushiSwap is a community-driven decentralized finance (DeFi) platform that lets users swap, earn, lend, borrow, and leverage cryptocurrency assets all from one place. Launched earlier this year, Sushi’s newest offering, Minimal Initial SushiSwap Offering (MISO), is a token launchpad that lets projects launch their own tokens on the Sushi network.
Unlike cryptocurrency coins that need a native blockchain and substantive groundwork, DeFi tokens are an easier alternative to implement, as they can function on an existing blockchain. For example, anybody can create their own “digital tokens” on top of the Ethereum blockchain without having to recreate a new cryptocurrency altogether.
Attacker steals $3 million in Ethereum via one GitHub commit
In a Twitter thread today, SushiSwap CTO Joseph Delong announced that an auction on MISO launchpad had been hijacked via a supply chain attack. An “anonymous contractor” with the GitHub handle AristoK3 and access to the project’s code repository had pushed a malicious code commit that was distributed on the platform’s front end.
A software supply chain attack occurs when an attacker interferes with or hijacks the software manufacturing process to insert their malicious code so that a large number of consumers of the finished product are adversely impacted by the attacker’s actions. This can happen when code libraries or individual components used in a software build are tainted, when software update binaries are “trojanized,” when code-signing certificates are stolen, or even when a server providing software-as-a-service is breached. Therefore, when compared with an isolated security breach, successful supply chain attacks produce far more widespread impact and damage.
In MISO’s case, Delong says that “the attacker inserted their own wallet address to replace the auctionWallet at the auction creation”:
The Miso front end has become the victim of a supply chain attack. An anonymous contractor by with the GH handle AristoK3 injected malicious code into the Miso front end. We have reason to believe this is @eratos1122.
864.8 ETH was stolen, address belowhttps://t.co/cDZeBqFV4P
— Joseph
Delong
(@josephdelong) September 17, 2021
The tweet above was deleted but has been made available here.
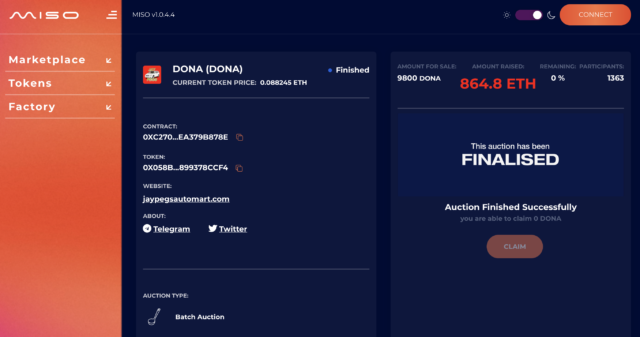
Through this exploit, the attacker was able to funnel out 864.8 Ethereum coins—around $3 million—into their wallet.
So far, only an automobile mart’s auction (1, 2) has been exploited on the platform, according to Delong, and affected auctions have all been patched. The finalized amount of the auction lines up with the number of stolen Ethereum coins.
SushiSwap has requested Know Your Customer records of the attacker from cryptocurrency exchanges Binance and FTX in an effort to identify the attacker. Binance said publicly that it is investigating the incident and offered to work with SushiSwap.
“Assuming the funds aren’t returned by 8a ET. We have instructed our lawyer [Stephen Palley] to file an IC3 complaint with the FBI,” said Delong.
Ars has seen the balance of the attacker’s wallet drop over the last few hours, indicating that the funds are changing hands. Recent transactions (1, 2) show the “Miso Front End Exploiter” returning the stolen currency to SushiSwap in the company’s pool called “Operation Multisig.”
It isn’t unusual for attackers and cybercriminals to return the stolen funds to their rightful owner out of fear of repercussions from law enforcement, as we saw in Poly Network’s $600 million heist.
But how did the attacker get GitHub access?
According to SushiSwap, the rogue contractor AristoK3 pushed malicious code commit 46da2b4420b34dfba894e4634273ea68039836f1 to Sushi’s “miso-studio” repository. As the repository appears to be private, GitHub is throwing a 404 “not found” error to those not authorized to view the repository. So how did the “anonymous contractor” get access to the project repository in the first place? Surely there must be a vetting process somewhere at SushiSwap?
Although anybody can offer to contribute to a public GitHub repository, only select individuals can access or contribute to private ones. And even then, the commits should ideally be verified and approved by trusted members of the project.
Cryptocurrency enthusiast Martin Krung, creator of the “vampire attack,” wondered if the attacker’s pull request was properly reviewed prior to being merged into the codebase, and he received insights from contributors:
I have seen PRs with more than 40+ files changed that instantly got approved. There is no code ownership.
— adamazad.eth (@adamzazad) September 17, 2021
A rough analysis (now removed by SushiSwap but backed up here) compiled by SushiSwap attempts to track down the attacker(s) and makes references to multiple digital identities. SushiSwap believes that GitHub user AristoK3 is associated with the Twitter handle eratos1122, although the latter’s response is inconclusive. “This is really crazy… Plz delete it and say ‘sorry’ to everyone… If not, I am going to share all of the MISO project [sic] that I have (You know what I have worked on MISO project very well),” responded eratos1122.
Because some of the digital identities mentioned in the analysis remain unverified, Ars is refraining from mentioning these until more information becomes available. We have reached out to Delong and the alleged attackers to learn more. We are awaiting their responses.